How to set up Mailvelope
Differentiation between Enigmail, Guard and Mailvelope
Enigmail, mailbox Guard and Mailvelope can be used to manage PGP key pairs. PGP keys enable communication via end-to-end encryption. This must be distinguished from transport encryption, which only secures the connection between one device or server involved in the transmission of the email and the next. Anyone who has access to a device involved in the email transmission can read the content when only transport encryption is used.
With PGP encryption, only the receiving person can view the email's content. Within PGP encryption, there are different application scenarios with varying levels of security.
If you use a secure device (PC or laptop), you will achieve the highest level of protection with the combination of a local email client and a local PGP management program (such as Thunderbird and Enigmail), since you always retain control over your private PGP key.
Mailvelope and mailbox Guard
You can use either mailbox Guard or Mailvelope.
With Mailvelope, the private PGP key is passed to the browser. The browser can be seen as an intermediary between the device and the Internet. The disadvantages associated with this are explained and weighed at the end of this article.
The Guard integrates the possibility of managing PGP keys into mailbox Office. In this case, the private key is also stored on our servers. Of course, it is safe there and additionally protected by a password, but this does not meet all security requirements.
This guide will focus on the use and setup of Mailvelope. In our Knowledge Base, however, you will find many other useful articles on the topic of PGP encryption and the mailbox Guard.
Mailvelope – overview
Mailvelope is a browser add-on that you can use in Firefox, Chrome and Edge to securely encrypt your emails with PGP when using webmail providers. If you use mailbox Office with Mailvelope, the following advantages arise:
- PGP encryption is integrated into the browser, with your private PGP key never stored on our servers. You can easily encrypt, decrypt and digitally sign emails with PGP.
- You can manage PGP keys on your computer.
- The use of a local GnuPG installation in combination with Mailvelope is possible and increases security.
Browser add-ons and therefore tools like Mailvelope may cause unwanted effects when using Drive or email attachments.
You will find Mailvelope in the respective web store of your standard browser – Google Chrome, Mozilla Firefox or Microsoft Edge.
Download Mailvelope
To use Mailvelope, first install the corresponding browser extension:
Confirm the necessary access permissions so that Mailvelope works correctly.
You can find further information and the current overview on the official project page: mailvelope.com.
Activate and set up Mailvelope
To use Mailvelope with mailbox Office, proceed as follows:
- In mailbox Office, navigate to the following path: All settings > Email encryption > PGP in web mailer
- Under Encryption expert with Mailvelope, click activate now.
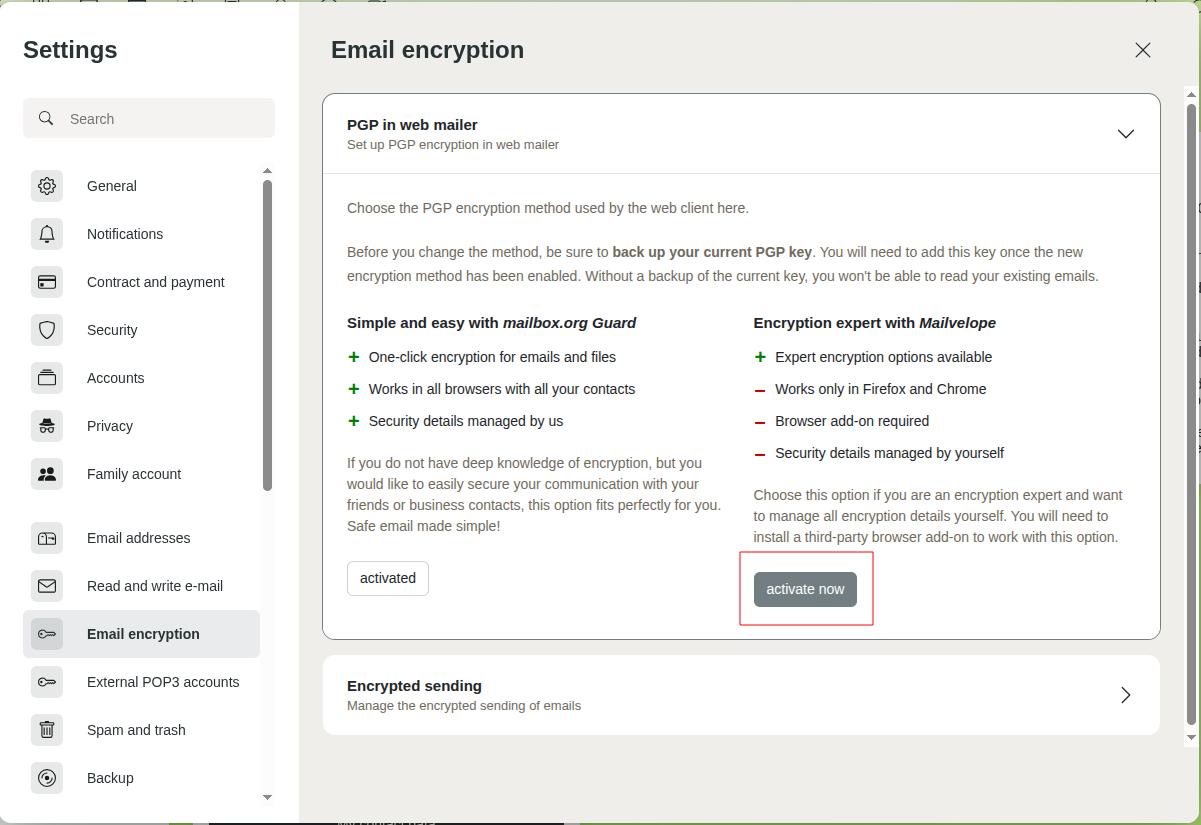
Activate Mailvelope in mailbox Office
- In mailbox Office, navigate to All settings > Security > Mailvelope.
- Click the button Mailvelope settings.
A new browser tab opens showing the Mailvelope settings.
If you already have your own PGP key pair, import your existing keys.
If you do not yet have a key pair, create your keys.
Set up Mailvelope with a previously unused mailbox without a PGP key pair
To set up Mailvelope if you have not yet configured mailbox Guard and do not have your own key pair:
- In Mailvelope's key management, click Create key.
- Enter the required information and create a complex password. Save it in a secure location, such as your KeePassXC password manager.
- Finally, click Create.
Your PGP key pair has been successfully created and is available in the Mailvelope add-on. You can now send emails using your PGP key pair.
Set up Mailvelope with a previously unused mailbox and an existing PGP key pair
If you have already created a key pair elsewhere and have not yet configured the Guard, please proceed as follows.
In Mailvelope's key management, click Import key.
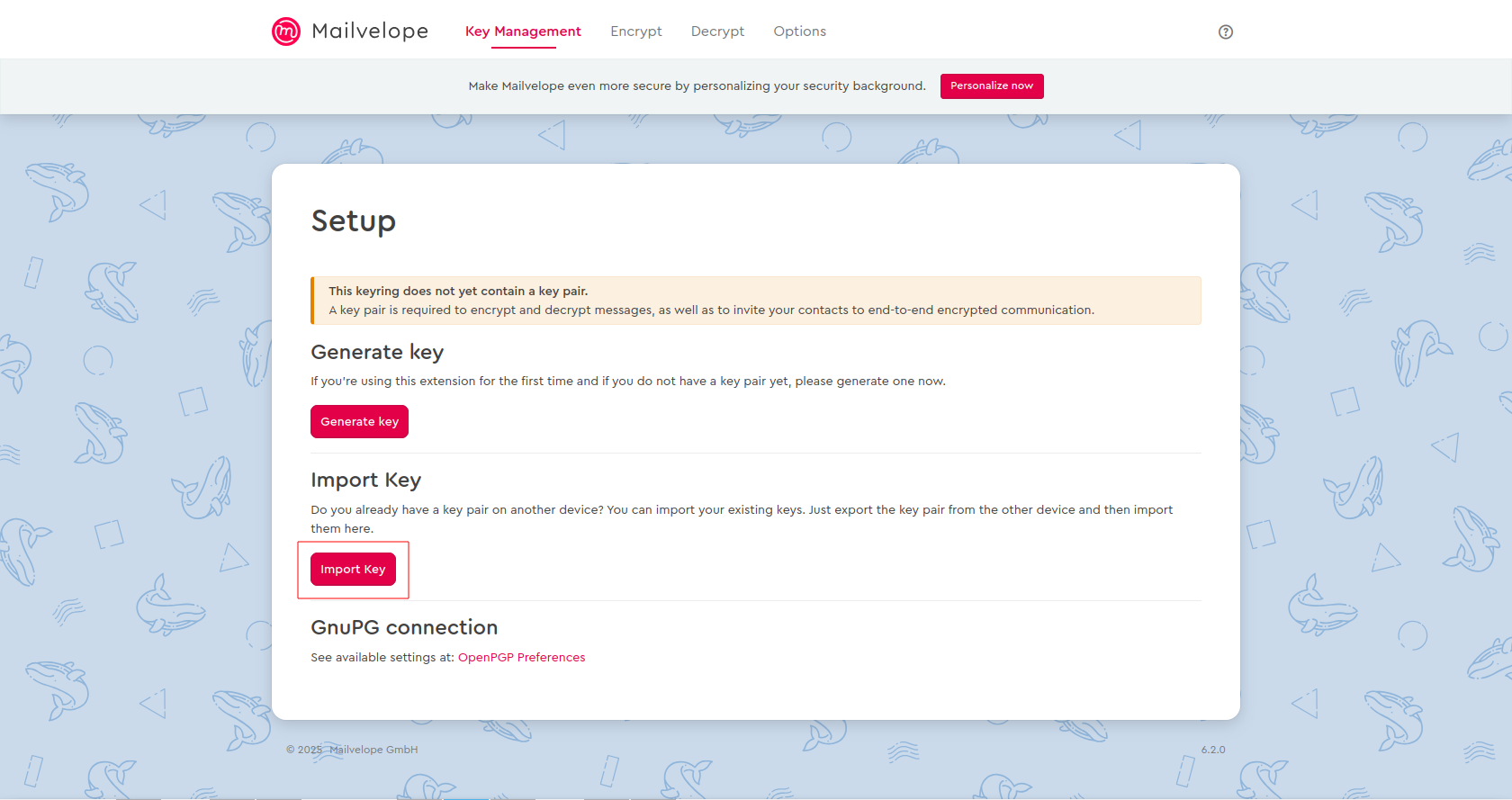
Import your key in Mailvelope
Now you have two import options:
- Import key as file: Use this function to select a (*.asc) file with keys from your hard drive and import it into Mailvelope.
- Import key as text: First copy the key(s) (multiple keys are also possible) to the clipboard. When you click Insert keys from clipboard, the keys are extracted from the text and transferred to the local keyring. Make sure to include both
-----BEGIN PGP PUBLIC KEY BLOCK-----and-----END PGP PUBLIC KEY BLOCK-----.
Import both your private and your public PGP key here.
Confirm the import of the key.
Done – you can now use Mailvelope with your own PGP key pair!
Switch from Guard to Mailvelope
Mailvelope and mailbox Guard cannot be used simultaneously. If you are currently using Guard, additional steps are required.
To switch from Guard to Mailvelope:
- Export your PGP key pair via the following path: All settings > mailbox Guard > Your keys
- If necessary, export the following public keys of your communication partners via the following path: All settings > mailbox Guard > Recipient keys
- Activate Mailvelope under All settings > Email encryption > PGP in web mailer.
- Import your key pair in Mailvelope as described under Set up Mailvelope with a previously unused mailbox and an existing PGP key pair.
Security notes on using Mailvelope
When using the Mailvelope add-on, there are some important security aspects to note:
- Your keys are stored on your computer in the local storage of the browser.
- Since local storage is used to store keys, Mailvelope is not suitable for use on foreign or insecure computers (e.g. in Internet cafés or while traveling).
- The HTML5 Security Cheat Sheet by OWASP recommends not storing security-relevant information in the browser's local storage, as this data could be compromised by XSS attacks.
- While there were still security drawbacks when using Mailvelope in relation to the old add-on architecture in Firefox 2003, this disadvantage has been eliminated with the introduction of Web Extensions in Firefox and since Mailvelope 2.0 (October 2017). Web Extensions also prevent CSP execution by default and thus XSS attacks.
- In Mailvelope, a local GnuPG installation can now also be used for key management. This further increases protection against such attacks and should be used.
Limitations due to Javascript
Javascript was not originally designed as a programming language for cryptographic applications. There are different approaches to assessing whether this is a disadvantage. Here are some arguments:
- What is considered a serious bug in other crypto implementations must be accepted in Mailvelope as a limitation due to Javascript – for example:
- It is not possible in Javascript to securely delete a private key from memory after use (“Overwriting memory – why?”).
- Normal behavior in Mailvelope is classified as a security vulnerability in the TOR project.
- Through side-channel attacks on the browser, it is possible to reconstruct the sequence of zeros and ones in the private key by observing code execution. However, the crypto implementation in Mailvelope (OpenPGP.js) runs mostly via the Web Crypto API of the browser, which reduces the risk of side-channel attacks.
- On the other hand, Javascript has the advantage of memory management. This prevents buffer overflows – which are often found in C/C++ implementations – from occurring in the first place.
Further notes
If you use Mailvelope to avoid storing your private key on mailbox servers, you may want to disable the Autocrypt function in the Mailvelope settings. This is not necessary when using mailbox, as we do not support this function via the client API.
