How to set up Mailvelope
About mailbox.org Guard and Mailvelope
As previously explained, Mailvelope is an alternative to mailbox.org Guard. If you are currently using mailbox.org Guard, migration will require some additional steps to be performed first.
In this case, please go directly to the section "Migrate from mailbox.org to Mailvelope" further down below and then come back here afterwards.
Note that only one mechanism can be used at any one time.
In order to proceed using Mailvelope with the mailbox.org Office go to: Settings  | mailbox.org | PGP in Webmailer
| mailbox.org | PGP in Webmailer
See the screen shot below. In the column titled “Encryption Expert with Mailvelope“, please click on the button "activate now".
Afterwards, log off from the mailbox.org Office and then on again to see the changes applied.
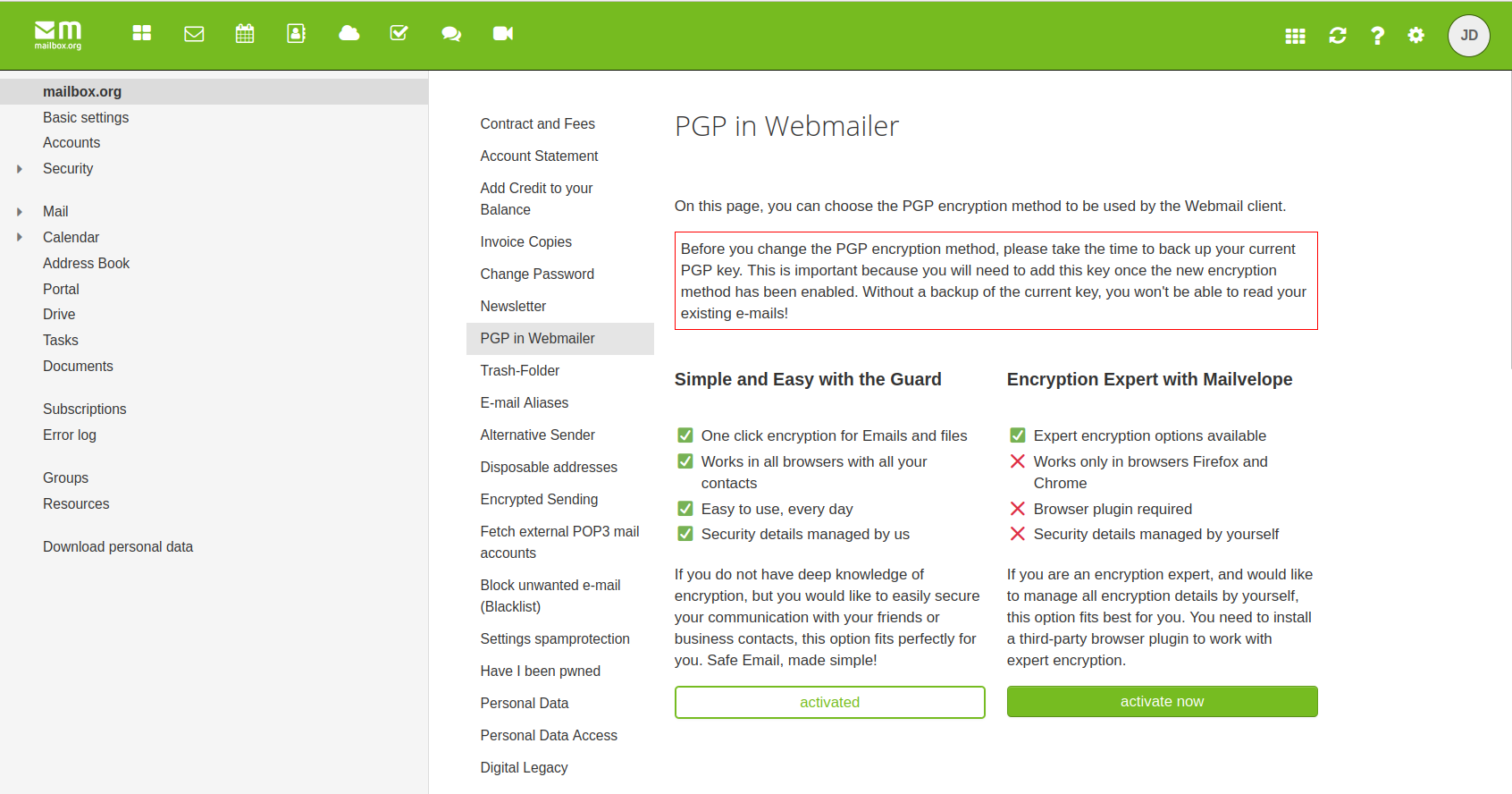 In the next step, go to Settings
In the next step, go to Settings  Security - Mailvelope - Download browser plugin
Security - Mailvelope - Download browser plugin
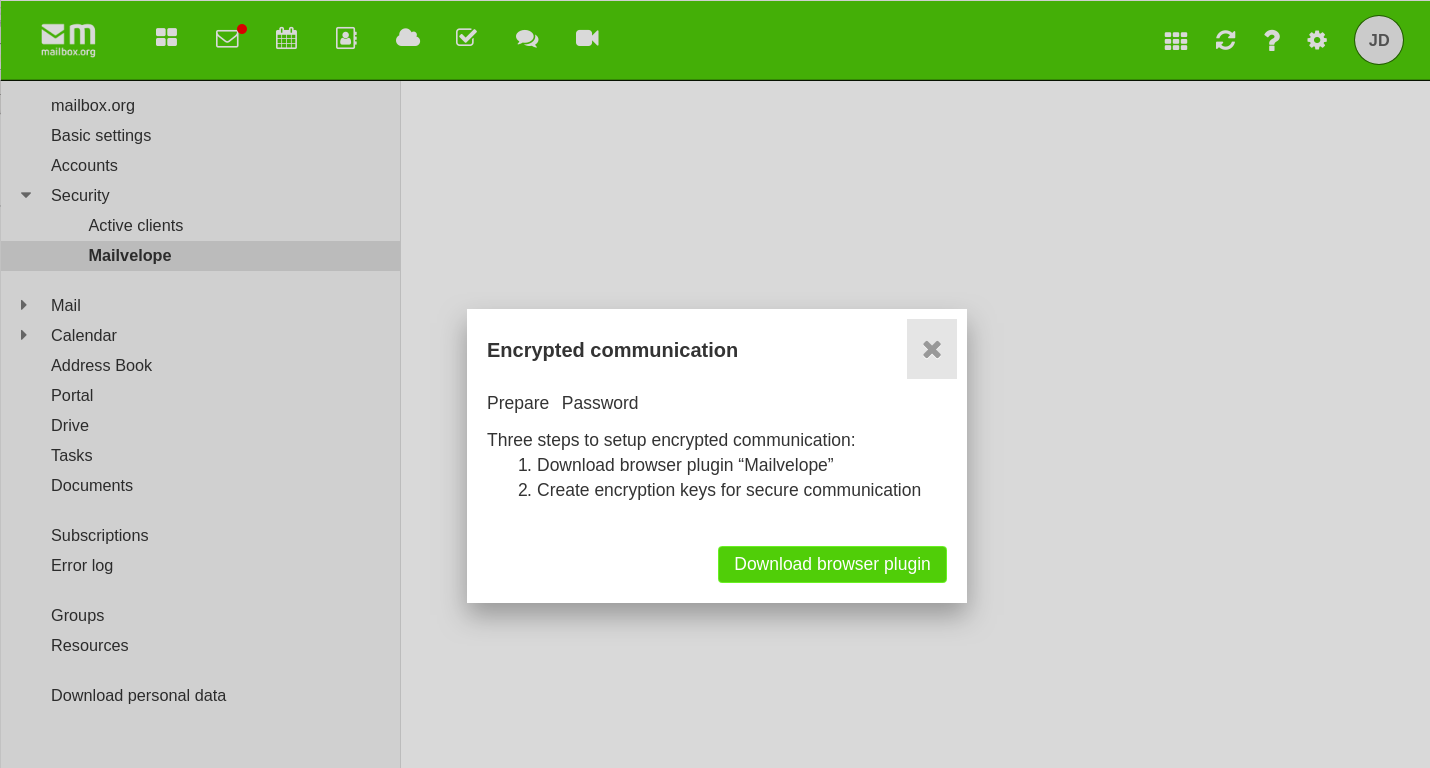
Depending on your browser choice, there may be a couple of security prompts that need confirming before the add-on can be installed, e.g.:
After the Mailvelope add-on was installed in your browser, the following page will appear:

There is nothing that needs to be done on this page.
If you have not used your inbox yet, proceed with the next step.
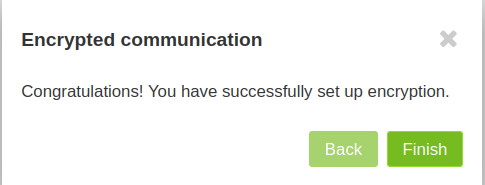
How to set up Mailvelope with a new inbox and without an existing PGP key pair
-
Follow the steps below to set up Mailvelope if mailbox.org Guard was not previously configured and there is no existing PGP key pair.
-
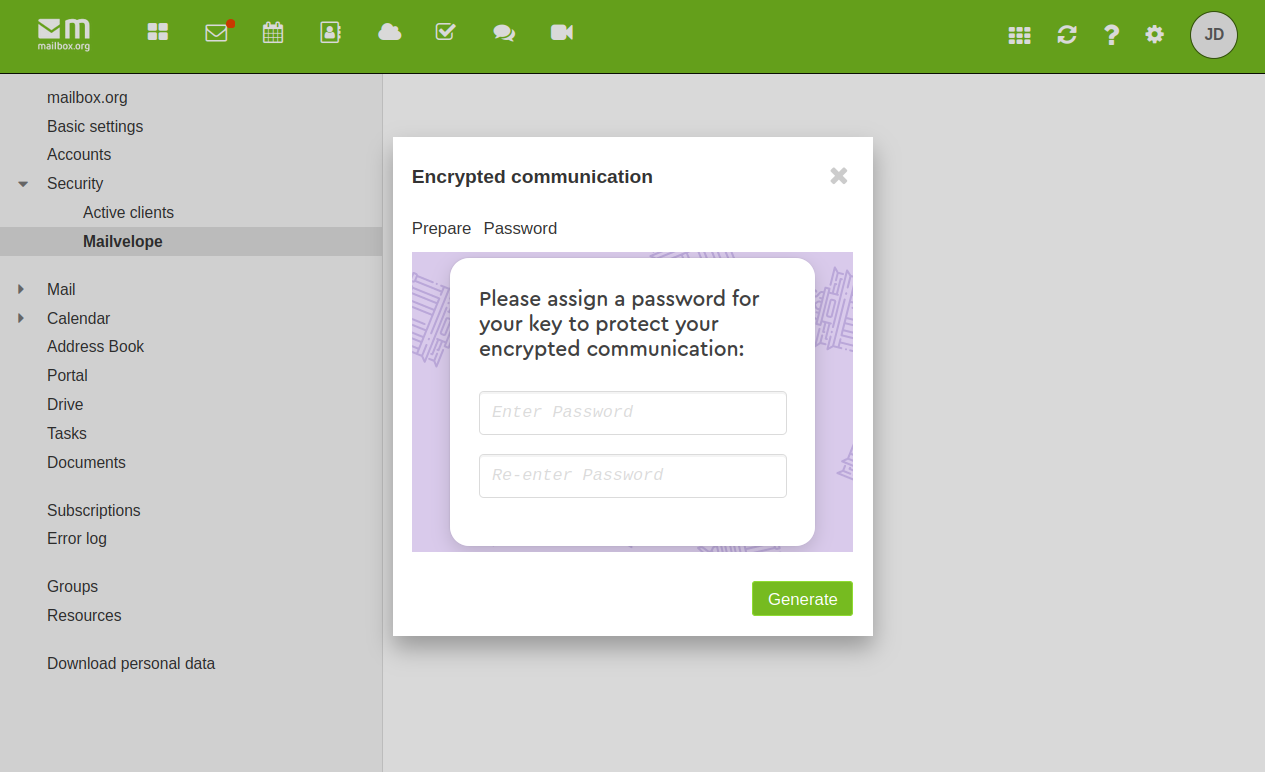
After installing the add-on, go to **Settings
 | Security | Mailvelope. A Mailvelope window will appear, asking you to assign a password to your key. Please make sure to choose a secure password and keep a note of this in a safe location, such as the KeepassXC password manager.
| Security | Mailvelope. A Mailvelope window will appear, asking you to assign a password to your key. Please make sure to choose a secure password and keep a note of this in a safe location, such as the KeepassXC password manager.
-
Your PGP key pair has now been created successfully and will be available in the Mailvelope add-on.
How to set up Mailvelope with a new inbox and an existing PGP key pair
-
If you created your PGP keys elsewhere but did not set up the mailbox.org Guard yet, then please proceed as follows:
-
Click on the Mailvelope symbol in your browser, which is next to the URL bar. Then, click on the “Let’s start” button.

-
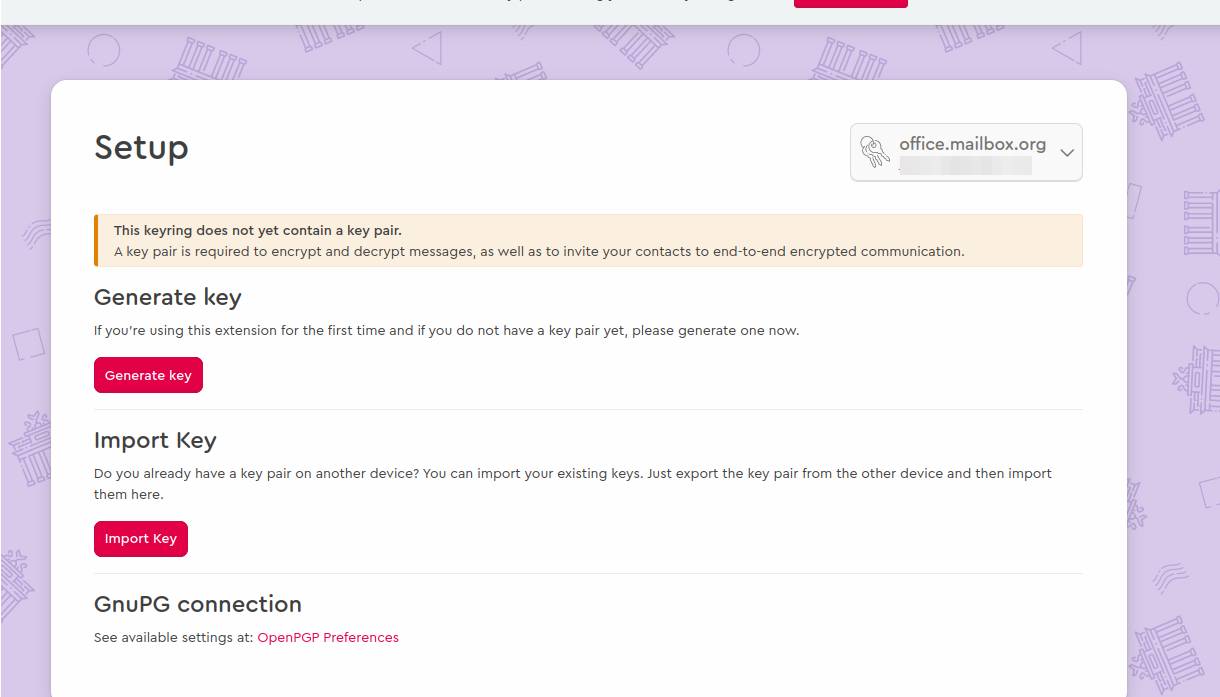
In the next step, click on "Import key"
Now, there are two different options:
-
Import key from file: If you saved your key(s) locally in an *.asc file, select that file to import the key into Mailvelope.
-
Import key as text: First, copy one or more keys to the clipboard but do not insert them just yet. Upon clicking on Import key from clipboard, the keys will be extracted from the copied text and transferred to your local key ring. Please make sure to include the parts
-----BEGIN PGP PUBLIC KEY BLOCK -----and-----END PGP PUBLIC KEY BLOCK -----in your text selection.Important note: You must import both your private and your public PGP key here.
-
-
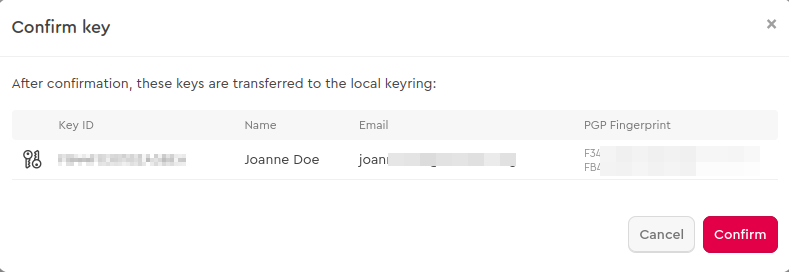
Now confirm the key import.**
** -
All done! You can now use Mailvelope with your existing PGP key pair.
How to set up Mailvelope for an existing mailbox.org Guard-protected inbox
This section is only relevant for those wanting to switch from mailbox.org Guard to Mailvelope.
-
Export your own PGP key pair, as well as any public keys of your communication partners, if required, as described in the bottom part of the following article:
https://kb.mailbox.org/en/business/security-privacy-article/activate-your-mailbox-org-guard -
Click on the Mailvelope symbol in your browser (next to the URL bar), then on the button “Let’s start”.

-
Click on "Import key"

Now, there are two different options:
-
- Import key from file: If you saved your key(s) locally in an *.asc file, select that file to import the key to Mailvelope.
-
-
Import key as text: First, copy one or more keys to the clipboard but do not insert them just yet. Upon clicking on Import key from clipboard, the keys will be extracted from the copied text and transferred to your local key ring. Please make sure to include the parts
-----BEGIN PGP PUBLIC KEY BLOCK -----and-----END PGP PUBLIC KEY BLOCK -----in your text selection.Important note
You must import both your private and your public PGP key here.
-
Now confirm the key import.

-
All done! You can now use Mailvelope with your existing PGP key pair.
Sending your first encrypted message
-
To send an encrypted message with Mailvelope, you need the public PGP key of the recipient. This key can be obtained from a public key server or directly as an *.asc file. Click here for an explanation of how to import this key into Mailvelope.
-
When composing a new e-mail in the mailbox.org Office, click on the padlock symbol (1.)
If you set up Mailvelope without using a previously created PGP key and also haven’t used mailbox.org Guard yet, you can send your message straightaway using your default key pair.
If you instead used one of the other methods and uploaded our own PGP key, you will be asked to set a password for the PGP key ring.
Note that this password is different from the password that secures the PGP key itself.
Background information
mailbox.org currently uses the traditional implementation of Mailvelope. That means keys are added to the mailbox.org key ring.
The latest recommendation is to use the main key ring instead. See the following link for reference: https://github.com/mailvelope/mailvelope/wiki/Guidelines-for-email-providers#notes-on-multiple-keyrings
We are going to implement this recommendation on our side with the objective to have it ready in the medium term.
Normally, users are not asked repeatedly for their key ring password. However, it is possible that you may need the password again in the future if the implementation changes, for example. Please make sure to keep the password in a safe location, such as KeepassXC.
Click on the button „Generate“ to finalize.
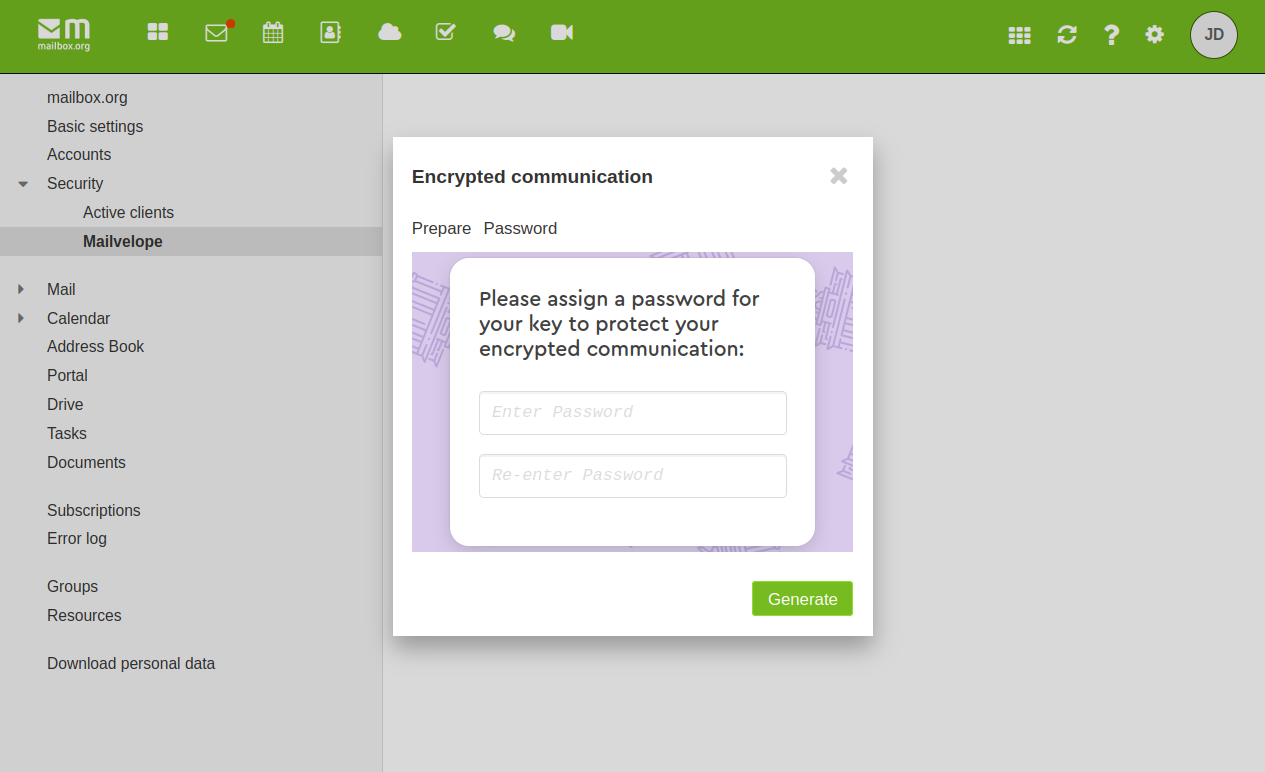
- The following status window will appear next.
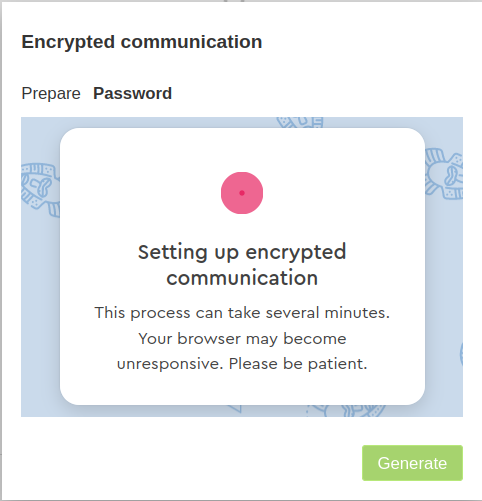
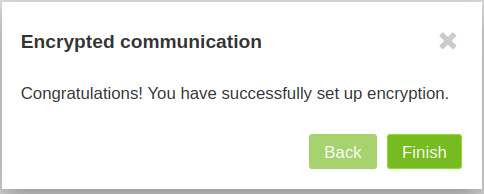
- After the process is complete, there will be another pop-up window to confirm that your e-mail communication through Mailvelope is now configured to use encryption.
Security implications
Using Mailvelope has certain security implications. Please do note the following:
-
Your keys will be stored locally, in the browser store on your computer.
-
Since the keys will be stored locally, Mailvelope is not suitable for use in potentially unsafe environments (e.g., any computers owned or used by other people, in Internet cafes, hotels, etc.)
-
The OWASP recommends in their HTML5 Security Cheat Sheet not to store any security-relevant information in the local browser store, because the information could be compromised through cross-scripting (XSS) attacks.
However, many browsers have improved their security features in recent years. While the old Firefox add-on architecture was not ideal for operating security-relevant software such as Mailvelope, this problem has been resolved with the introduction of Web extensions in Firefox a__nd the corresponding Mailvelope 2.0 extension (October 2017). Web extensions will normally prevent the execution of CSP and so, block cross-scripting attacks unless specifically configured to behave differently. -
Mailvelope permits the use of a local GnuPG installation for key management, which we recommend because this further increases protection against attacks.
-
Javascript is a programming language that was not designed with security in mind. It is therefore of limited use for cryptography applications generally. Some of the things that would be absolute no-nos in other cryptography implementations have to be accepted as a limitation in Mailvelope because it uses Javascript.
-
There are different perspectives on the suitability of Java and Javascript for secure communication, for example:
-
With Javascript, it is not possible to securely remove a key from main memory after use. (Overwriting memory - why?).
The TOR project considers this behavior of Mailvelope a vulnerability. -
Browsers can be subjected to side-channel attacks, which makes it possible to track and reconstruct the low-level encoding of an encryption key during code execution. However, the implementation of Mailvelope (OpenPGP.js) largely relies on the browser Web cryptography API, so there is a certain level of protection against side-channel attacks.
-
There is an advantage that Java has over other languages. Java uses built-in memory management, which decreases the risk of buffer overflows. These would be more likely in C/C++ implementations.
-
-
If your motivation for using Mailvelope is primarily to avoid storing your key on the mailbox.org servers, then you will want to disable the "Autocrypt" feature in the Mailvelope settings (German).
Doing so won't be required if you use mailbox.org, as we do not support this feature through the client API.
In our view Mailvelope offers sufficient security, also thanks to the continuous improvements that have been made over the years.
However, for the reasons outlined above, we cannot recommend the use of Mailvelope in scenarios that require high security standards.