The Tor exit node of mailbox.org
In order to promote anonymity on the internet and to protect our customers against unwarranted surveillance, we decided to operate a dedicated Tor exit node in our data center. This Tor node will provide added security for our customers who are also users of the anonymisation service Tor Onion Router at the same time.

In the last few years, there have been repeated reports about malicious Tor exit nodes, some of which apparently used false SSL certificates to attempt man-in-the-middle attacks on encrypted HTTPS connections (For instance, in 2013: Connections to Wikipedia or IMAPS connections).
In order to make sure such attacks won't be possible on mailbox.org services, we offer
- a dedicated node within our data centre that all Tor users should configure as the exit server for accessing mailbox.org addresses.
- Alternatively, you can also use the Tor Hidden Service **xy5d2mmnh6zjnroce4yk7njlkyafi7tkrameybxu43rgsg5ywhnelmad.onion** (v3) for accessing our SMTP, POP3, IMAP, or XMPP servers.
1. Add MapAddress configuration settings for the Tor daemon
Users can configure their Tor daemon to use a specific exit node for accessing particular servers in a domain. This is the way to go if you are a Tor user and also a customer of mailbox.org, because we have an exit node set up that is located within our own data centre and can therefore facilitate a secure connection to your mailbox.org services. This solution allows using mailbox.org without having to specify an Onion host name, avoids any SSL certificate validation problems, and best of all, you can use your mailbox.org Office suite in the Web browser as usual.
To start, use a text editor to open the file in path Browser/TorBrowser/data/Tor/torrc (see also the Tor FAQ). If you have just installed the Tor Browser Bundle, then you need to start the Tor browser at least once and then close it again to see that file. With the configuration file open, add the following lines:
MapAddress mailbox.org mailbox.org.85D4088148B1A6954C9BFFFCA010E85E0AA88FF0.exit MapAddress _.mailbox.org _.mailbox.org.85D4088148B1A6954C9BFFFCA010E85E0AA88FF0.exit
The settings above make sure that any data traffic to the mailbox.org servers will be channeled through the Tor network to eventually exit through the node that sits in our data centre. This scenario resembles something like an anonymous VPN connection, one might say.
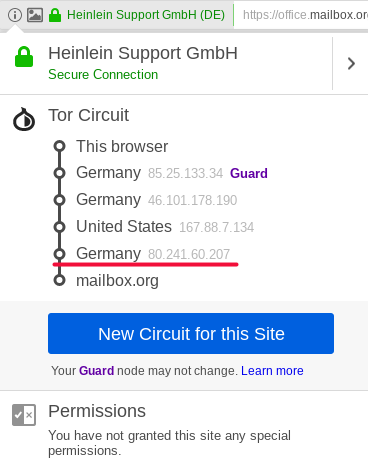
If everything has been configured correctly, the last Tor hop should be the IP address "80.241.60.207". You can verify this by opening the webpage of mailbox.org and then clicking the info-button right beside the web address field in the Tor browser.
2. Use the Tor Hidden Service instead
As an alternative, we also offer the Tor Hidden Service xy5d2mmnh6zjnroce4yk7njlkyafi7tkrameybxu43rgsg5ywhnelmad.onion (v3) for our e-mail and Jabber/XMPP servers.
However, note that it is not possible to access the web interface of mailbox.org this way.
In Mozilla Thunderbird, you can use the Tor Hidden Service directly as an SMTP, IMAP, or POP3 server entry – here, there is no need to adjust the configuration of your Tor daemon.
In a Jabber/XMPP client, the Tor Hidden Service can be set as connect server (this setting can usually be found in the advanced options).
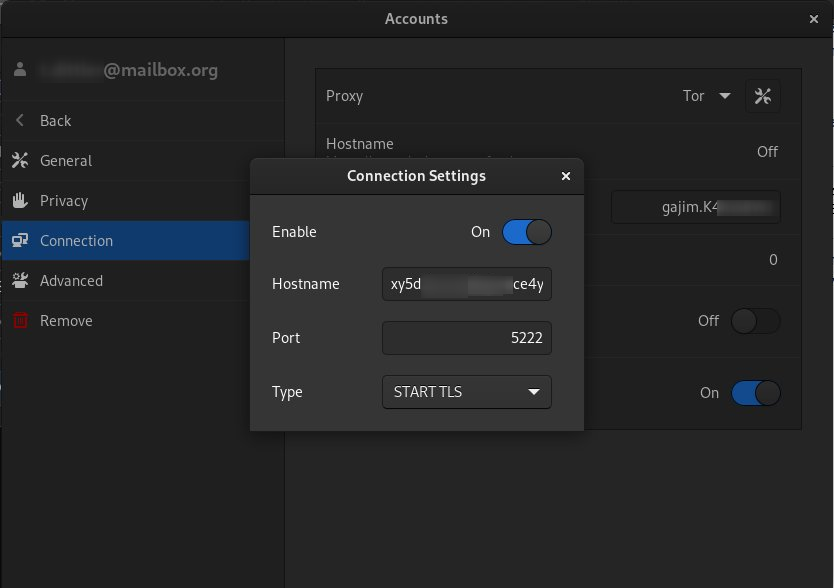
Usage of Gajim Messenger with Tor v3 Address
A distinct disadvantage of the Tor Hidden Service is that upon connecting, users will experience SSL errors, because the certificate used for transport security is issued for the domain mailbox.org and not the domain of the hidden service. Consequently, users need to verify the SSL certificate manually.
For further reading, please refer to How to configure the Tor Browser