How to set DKIM entries with TXT fields in the DNS
DKIM through TXT is deprecated
Please note that this article describes a procedure that is deprecated. It’s generally better to follow best practice and set DKIM entries through the CNAME record. For all setups made in 2021 or later we recommend specifying DKIM information with CNAME records in the DNS. Instead of using TXT entries as described below, please follow the guidance in the following article instead: SPF, DKIM, and DMARC: How to improve spam reputation and avoid bounces.
mailbox.org changed their configuration recommendations for DKIM back in 2021. Previously, we recommended to set DKIM entries as described below by creating TXT records. While this method will continue to work, it comes with a major disadvantage: Whenever we need to make changes to our keys, all TXT entries referring to these keys will become invalid, causing users a lot of hassle as a result. Customers and admins who still use TXT entries for DKIM should act now to avoid their e-mails being increasingly flagged as spam. Those who set up their DKIM key with a CNAME entry don’t have this problem as they don’t need to make any changes to the CNAME entry - the key reference there will always remain valid. Another advantage is that any character limitations that restrict the maximum length of a DKIM key, which are imposed by some hosting providers, can be avoided by using CNAME.
Up until 2019, mailbox.org would receive the DKIM keys from our customers and use these to generate custom keys. From 2019 onwards, we have switched to the use of generic keys. If you are still using keys that were created through the procedure below, please ask us to remove these keys and use CNAME entries instead. To get this done, simply create a support ticket at https://support.mailbox.org
Setting DKIM entries in TXT fields
In order to enable DKIM for your embedded domain, it is necessary for you to store one of the generic keys listed below at your domain provider. The procedure to do this will normally be similar to the steps outlined below:
- Open the DNS settings at your provider and create a "TXT" entry.
- Insert the character string "
MBO0001._domainkey" into the field that is labelled either "Host", "Name", or "Hostname". Please note that there may be different spelling variants for the label across different providers (also see the info box above). - Insert the following entries as :
- "Value":
- "Destination"
- "Target" (of the field labelled "TXT", "Text", or similar)
DNS TXT entry for DKIM
v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA2K4PavXoNY8eGK2u61LIQlOHS8f5sWsCK5b+HMOfo0M+aNHwfqlVdzi/IwmYnuDKuXYuCllrgnxZ4fG4yVaux58v9grVsFHdzdjPlAQfp5rkiETYpCMZwgsmdseJ4CoZaosPHLjPumFE/Ua2WAQQljnunsM9TONM9L6KxrO9t5IISD1XtJb0bq1lVI/e72k3mnPd/q77qzhTDmwN4TSNJZN8sxzUJx9HNSMRRoEIHSDLTIJUK+Up8IeCx0B7CiOzG5w/cHyZ3AM5V8lkqBaTDK46AwTkTVGJf59QxUZArG3FEH5vy9HzDmy0tGG+053/x4RqkhqMg5/ClDm+lpZqWwIDAQAB
The following figure shows how these values end up in providers' dialogues. When setting up DKIM, note that the DNS entry forms at different providers can have different layouts. Please see the examples below to get an idea of how the forms and entries would look like at Hetzner, Netcup and Inxw (Figures 1 to 3).
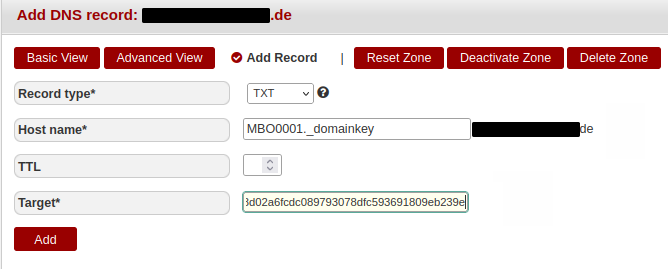
Figure 1: At Hetzner, the DKIM key needs to go into the "Target*" field
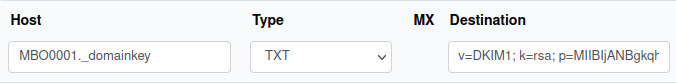 falsch, weil deutscher Screenshot?
falsch, weil deutscher Screenshot?
Figure 2: At Netcup, the field is called "Destination"
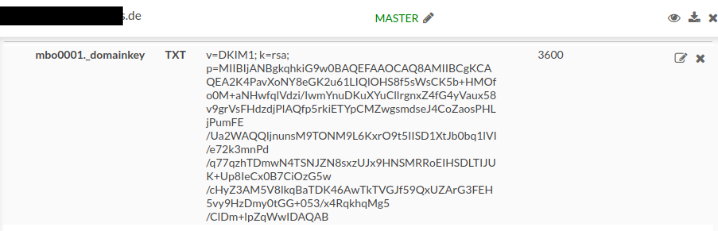
Figure 3: At INWX, the inputs fields are organised as a table
Troubleshooting
If the above doesn’t work for you, then please use the procedure recommended by mailbox.org and described in the article "SPF, DKIM, and DMARC: How to improve spam reputation and avoid bounces". Using TXT fields for DKIM-Keys has several flaws that are prone for errors. However, you can try to use a different key: Try using the entry "MBO0002._domainkey" as a subdomain and enter the following key:
Alternative key for the DKIM TXT entry in the DNS
v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAqxEKIg2c48ecfmy/+rj35sBOhdfIYGNDCMeHy0b36DX6MNtS7zA/VDR2q5ubtHzraL5uUGas8kb/33wtrWFYxierLRXy12qj8ItdYCRugu9tXTByEED05WdBtRzJmrb8YBMfeK0E0K3wwoWfhIk/wzKbjMkbqYBOTYLlIcVGQWzOfN7/n3n+VChfu6sGFK3k2qrJNnw22iFy4C8Ks7j77+tCpm0PoUwA2hOdLrRw3ldx2E9PH0GVwIMJRgekY6cS7DrbHrj/AeGlwfwwCSi9T23mYvc79nVrh2+82ZqmkpZSTD2qq+ukOkyjdRuUPck6e2b+x141Nzd81dIZVfOEiwIDAQAB
Entries for BIND DNS Servers
Administrators running their own BIND DNS server can enter their DKIM Keys directly in BIND's configuration files:
DKIM configuration for a Bind DNS server
MBO0002._domainkey IN TXT ( "v=DKIM1; k=rsa; " "p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAqxEKIg2c48ecfmy/+r" "j35sBOhdfIYGNDCMeHy0b36DX6MNtS7zA/VDR2q5ubtHzraL5uUGas8kb/33wtrW" "FYxierLRXy12qj8ItdYCRugu9tXTByEED05WdBtRzJmrb8YBMfeK0E0K3wwoWfhI" "k/wzKbjMkbqYBOTYLlIcVGQWzOfN7/n3n+VChfu6sGFK3k2qrJNnw22iFy4C8Ks7" "j77+tCpm0PoUwA2hOdLrRw3ldx2E9PH0GVwIMJRgekY6cS7DrbHrj/AeGlwfwwCS" "i9T23mYvc79nVrh2+82ZqmkpZSTD2qq+ukOkyjdRuUPck6e2b+x141Nzd81dIZVf" "OEiwIDAQAB" )