The mailbox HKPS key server
Our HKPS Keyserver
If you use the mailbox interface with Guard, the PGP keys of other Guard users are found automatically.
For external senders and users of mail clients such as Thunderbird, we provide an HKPS keyserver. This offers verified PGP keys of mailbox users for import into the local keyring.
Unlike other keyservers, the keyserver from mailbox only provides verified keys: it is not possible to upload a false key for someone else’s mail address.
Using the HKPS keyserver via the command line
On Linux, you can use the gpg2 program via the command line to search our keyserver for PGP keys of mailbox users. Use the following command:
- Address of the keyserver:
hkps://pgp.mailbox.org
Example:
gpg2 --keyserver hkps://pgp.mailbox.org --search max.mustermann@mailbox.org
Please note that you should use at least GnuPG 2.0 (gpg2), since our keyserver is only accessible via an SSL-encrypted connection. Versions 1.x of GnuPG (gpg) support SSL encryption for keyservers only with the gnupg-curl add-on module.
There are GnuPG implementations available for other operating systems as well. If you are using Windows or macOS, for example, you can find a link to a suitable version for your operating system on the GnuPG download page.
Using the HKPS keyserver with Enigmail for Thunderbird
If you use the Enigmail add-on for the Thunderbird mail client to manage your encrypted mail, you can add the HKPS keyserver from mailbox in the Enigmail configuration under the Keyserver tab.
You will see this tab after clicking on Expert Options and Display Menus in the Enigmail settings. If you then need the key of a mailbox user, you can simply select this keyserver during the key search to import the corresponding verified key.
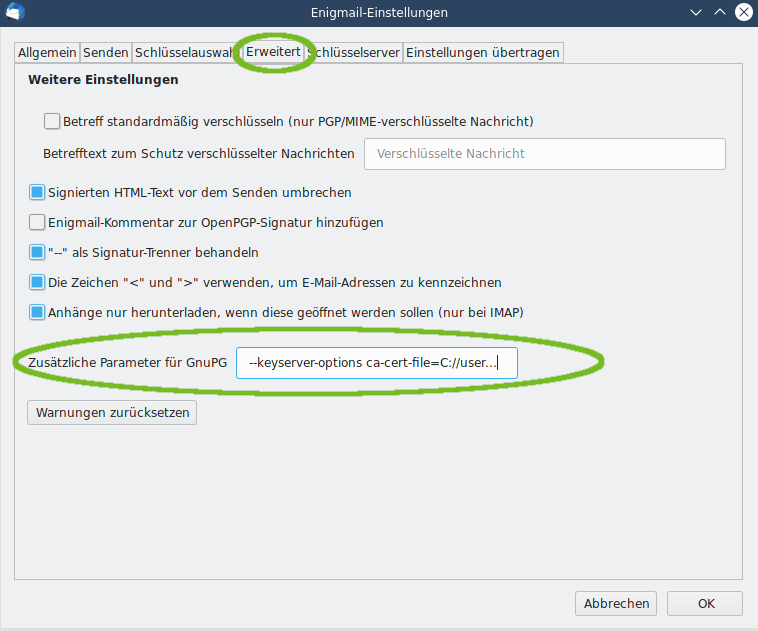
Figure 1: Enigmail settings.
Known issues with HKPS keyservers
Some installations of GnuPG2 may not be able to locate the CA root certificates provided by the operating system due to the SSL library used. The key search then fails with a general server error.
In addition to GPG4WIN, Ubuntu 16.04 and some other Linux distributions are also affected.
To resolve the issue, you need to tell GnuPG which CA root certificate should be used to validate the server certificate.
Ubuntu 16.04
Open the configuration file:
$HOME/.gnupg/dirmngr.conf
with a text editor of your choice and add the following line:
hkp-cacert /etc/ssl/certs/ca-certificates.crt
Auto-Key-Locate
You can configure GnuPG to automatically search our keyserver for a matching key if it is not available locally. This feature is called auto-key-locate.
To enable it, edit the gpg.conf configuration file with a text editor of your choice. (macOS users can also use the GPGPreferences program for this.)
The gpg.conf file is located:
-
on Linux: in the directory
$HOME/.gnupg -
on Windows: in the directory
%APPDATA%\GnuPG
Add the following line to enable auto-key-locate:
auto-key-locate keyserver keyserver-URL hkps://pgp.mailbox.org
Privacy notice
The auto-key-locate function is controversially discussed among privacy enthusiasts. In addition to simplifying and automating the key search, it also has potential implications for privacy:
The operator of the keyserver could log access and thus draw conclusions about who is communicating with whom. GnuPG explicitly points out these possible implications in its documentation.
However, if the operator of the keyserver is also the operator of the mail server (as with mailbox), these concerns are unfounded: The mail server already knows all active mail contacts of the user and does not gain any additional information through the key search.
Using our HKPS keyserver for your own domain
If you retrieve or send the mail of your own domain via mailbox, you can enable PGP clients to automatically find the responsible PGP server from mailbox and fetch the keys there.
To do this, you need to add a special SRV DNS record to your domain, as in the following example for the domain example.com:
hkps._tcp.example.com. IN SRV 1 1 443 pgp.mailbox.org
