SSL-TLS encryption at mailbox
Transport path of a mail with TLS transport encryption
The transport path of a mail between different mail providers can be secured with TLS transport encryption. TLS stands for Transport Layer Security and should not be confused with end-to-end encryption such as PGP and the Guard.
mailbox always shows you before sending a mail whether the transmission is secure. Figure 1 explains the possibilities:
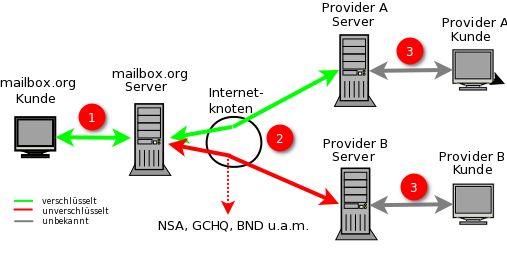
Figure 1: Visual representation of an emails transport route with TLS transport encryption
For the connection between customers and the mailbox servers, transport encryption according to the current state of the art is always enforced. Also, for the connection between the mailbox servers and the servers of other providers, all prerequisites are in place to establish secure transport encryption. However, with some providers, it may occur that either no encrypted connection is possible or the offered encryption no longer meets current security requirements. The recipients are located behind the mail server of the respective provider.
At this point, it is theoretically possible that the provider allows access using outdated transport encryption standards.
Mail sending policies at mailbox
The following policies are enforced by mailbox by default when sending mails:
-
If provider A has published a TLSA/DANE record with the fingerprint of the server's X.509 certificate via DNSSEC, then transport encryption with this certificate will be enforced. As a customer of mailbox, you can rely on the fact that the mail is sent over a secure channel to the recipient’s provider.
-
When you send a mail to other mail servers, mailbox will by default attempt to establish TLS encryption. If our servers have already successfully established a TLS-encrypted connection to the respective server of another provider, we store the highest possible encryption and will enforce this kind of transport encryption for this connection in the future.
-
For the servers of some mail providers, it was and still is not possible to establish a TLS-encrypted connection. In this case, the mail will be sent via an unencrypted connection. If your mail is not end-to-end encrypted (e.g. via PGP), any server through which the mail is routed from our mail server to the recipient's mail server can read or modify the plain text of your message (see also: man-in-the-middle attack).
Display of the transport encryption level
When composing a new mail in mailbox Office, you are automatically informed about the security level of transport encryption when selecting the recipient and can then decide whether you want to send the mail. This information is displayed by a symbol next to each recipient address. The recipients (or the mail servers of their providers) are classified in three levels:
-
TLS-capable plus DANE/DNSSEC (4):
If the target system meets a sufficiently high TLS security standard and also offers DANE- and DNSSEC-secured connections, you will see this special connection protection indicated by a green raised thumb and the info “DANE ok”. -
TLS-capable (5):
If the target system supports normal TLS encryption, you will recognize this by a green outlined raised thumb. -
No transport encryption possible:
In this case, you will be warned with a red “no SSL” (6). -
No information available:
If we have no information about the target system yet, a grey “SSL?” is displayed (7).
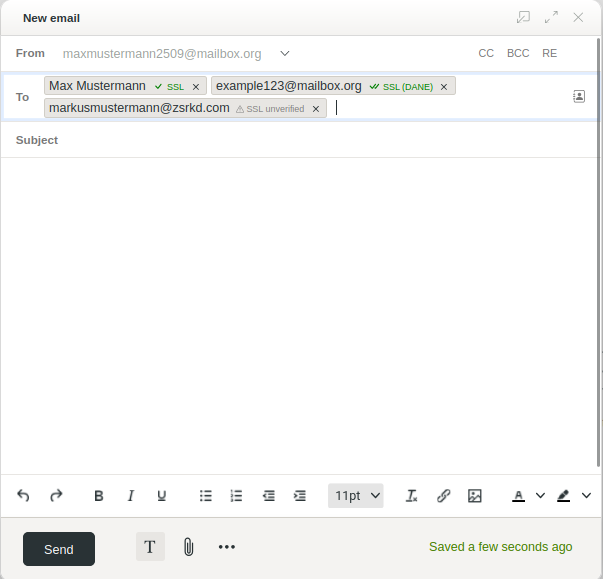
Figure 2: Even when composing an email, mailbox displays the encryption options for the delivery route.
You can also hover over the encryption symbol with your mouse to get further information about the encryption algorithms and the TLS version used:
SSL and TLS
The term “SSL” (Secure Socket Layer) has become established as a synonym for transport encryption, since the name of the first transport encryption was Secure Sockets Layer.
Better to block than to send unencrypted
As the following illustration shows, there are two situations in which mailbox’s transport encryption cannot take effect – namely when the message reaches network areas that are not under the control of mailbox.
This is the case if the receiving server does not offer current transport encryption or if an outdated mail client is allowed to establish the connection with the recipient server.
You can minimize such risks by additionally activating an alias at @secure.mailbox.org in addition to your regular mail address at @mailbox.org.
You should always use this address (for example, example@secure.mailbox.org instead of example@mailbox.org) if a secure transport encryption between mail servers must be guaranteed – in particular if unencrypted deliveries must not be tolerated under any circumstances.
Activation is easy via the option field Enable under:
All settings | Mail encryption | Encrypted sending
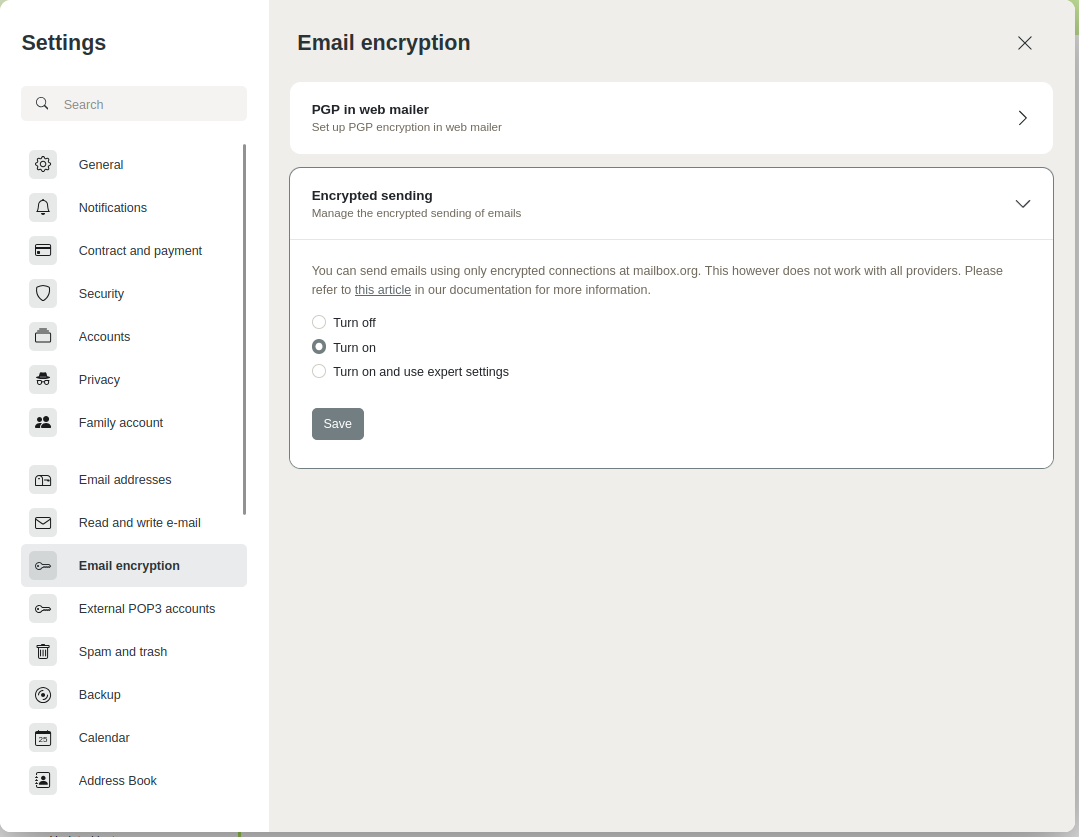
Figure 3: Here you can enable encrypted sending in mailbox.
Aliases with secure.mailbox.org
When you enable encrypted sending, mailbox automatically sets up a corresponding @secure.mailbox.org address for each of your aliases.
As soon as you select an @secure.mailbox.org address as the sender (e.g. myalias@secure.mailbox.org), our mail servers will only send this mail via a TLS-encrypted connection at minimum. If the recipient's provider does not offer this, the mail cannot be sent and you will receive an error message.
Replies to your secure.mailbox.org address
To ensure that replies to transport-encrypted messages are not accidentally sent unencrypted – and thus potentially disclose confidential content – mailbox also enforces the same encryption standards on receipt.
This is realized through special rules for the @secure.mailbox.org address. If the mail server of the communication partner cannot establish a connection with active transport encryption, the connection to the mailbox servers will fail.
In this case, the sender will receive a delivery notification stating that the mail could not be delivered.
Important: The @secure.mailbox.org address has no effect on the connection path from the sender's device to their mail server. For example, an outdated mail client may still use the insecure TLS 1.0 protocol – making the connection between the device and the sending server potentially insecure.
Current security requirements
For the @secure.mailbox.org address, mailbox exclusively uses current and secure encryption methods.
These are regularly reviewed – outdated or insecure methods are consistently removed.
